June 14, 2023
Spyware trojan activity decreased by 27.89%. Once again, different variants of a specific spyware trojan (including Android.Spy.5106 and Android.Spy.4498) hidden in some unofficial modifications of WhatsApp messenger were most often detected.
The number of banking trojan attacks increased by 32.38%, and the number of Android.Locker ransomware attacks increased by 14.83%, compared to March.
During April, Doctor Web’s virus analysts discovered other malicious apps from the Android.FakeApp family. Attackers used them in various fraudulent schemes. Moreover, cybercriminals distributed a trojan app from the Android.Joker family via Google Play. This malware subscribed victims to paid services.
PRINCIPAL TRENDS IN APRIL
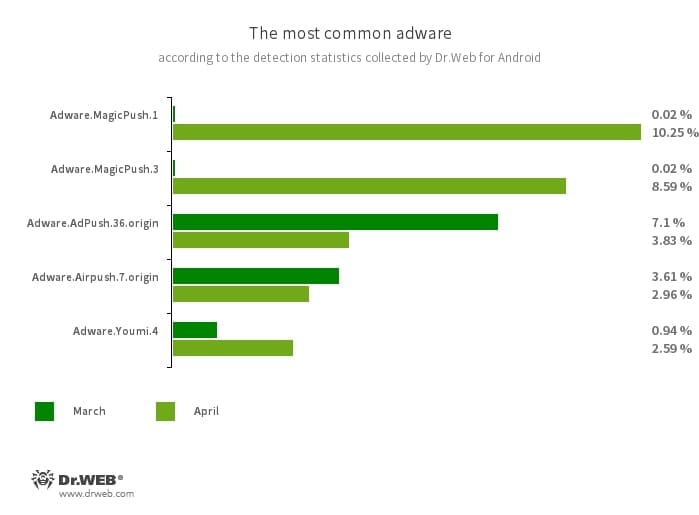
- An increase in Android.MobiDash adware trojan activity
- A decrease in Android.HiddenAds adware trojan activity
- An increase in banking trojan and ransomware trojan activity
- The discovery of other threats on Google Play
According to statistics collected by Dr.Web for Android
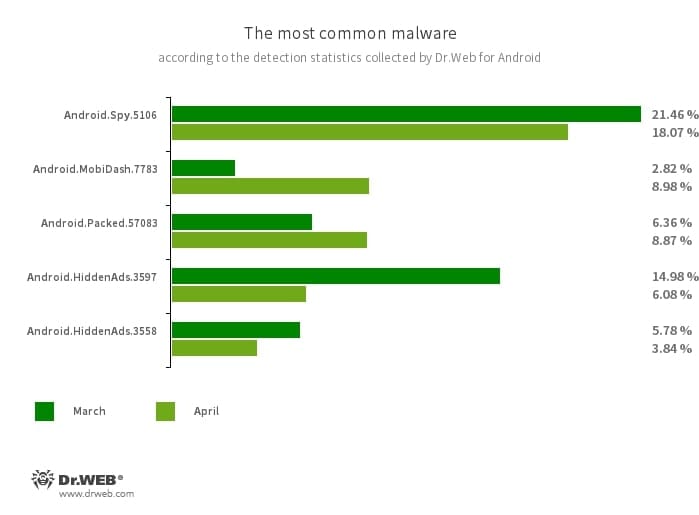
- Android.Spy.5106
- The detection name for a trojan that represents itself as modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes containing remotely configurable content.
- Android.MobiDash.7783
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.HiddenAds.3597
- Android.HiddenAds.3558
- Trojan apps designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
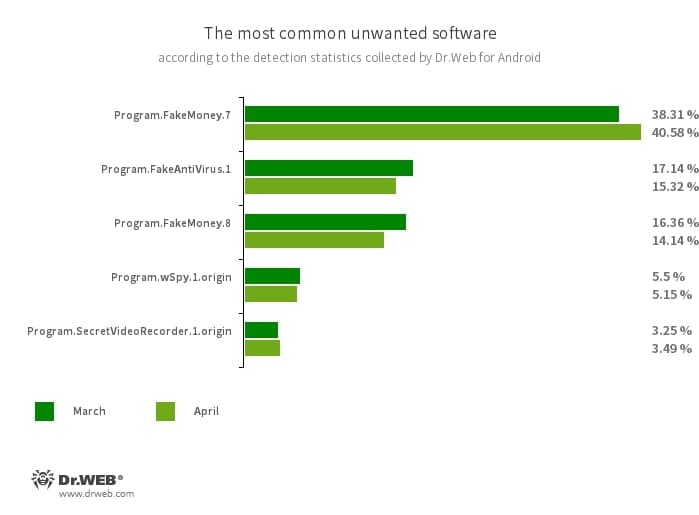
- Program.FakeMoney.7
- Program.FakeMoney.8
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to the phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
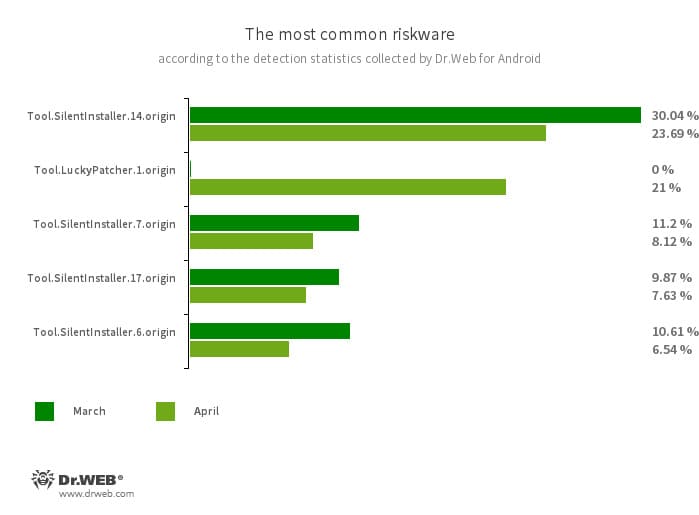
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.17.origin
- Tool.SilentInstaller.6.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.LuckyPatcher.1.origin
- A tool that allows apps installed on Android devices to be modified (i.e., by creating patches for them) in order to change the logic of their work or to bypass certain restrictions. For instance, users can apply it to disable root access verification in banking software or to obtain unlimited resources in games. To add patches, this utility downloads specially prepared scripts from the Internet, which can be crafted and added to the common database by any third-party. The functionality of such scripts can prove to be malicious; thus, patches made with this tool can pose a potential threat.
- Adware.MagicPush.1
- Adware.MagicPush.3
- Adware modules embedded into Android applications. They render pop-up banners over the OS user interface when such hosting apps are not in use. These banners contain misleading information. Most often, they inform users about suspicious files that have allegedly been discovered, or they offer to block spam for users or to optimize their device’s power consumption. To do this, they ask users to open the corresponding app containing such an adware module. Upon opening the app, users are shown an ad.
- Adware.AdPush.36.origin
- It displays notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, this module collects a variety of confidential data and is able to download other apps and initiate their installation.
- Adware.Airpush.7.origin
- A member of a family of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Youmi.4
- The detection name for an unwanted adware module that adds advertizing shortcuts onto the Android OS home screen.
Threats on Google Play
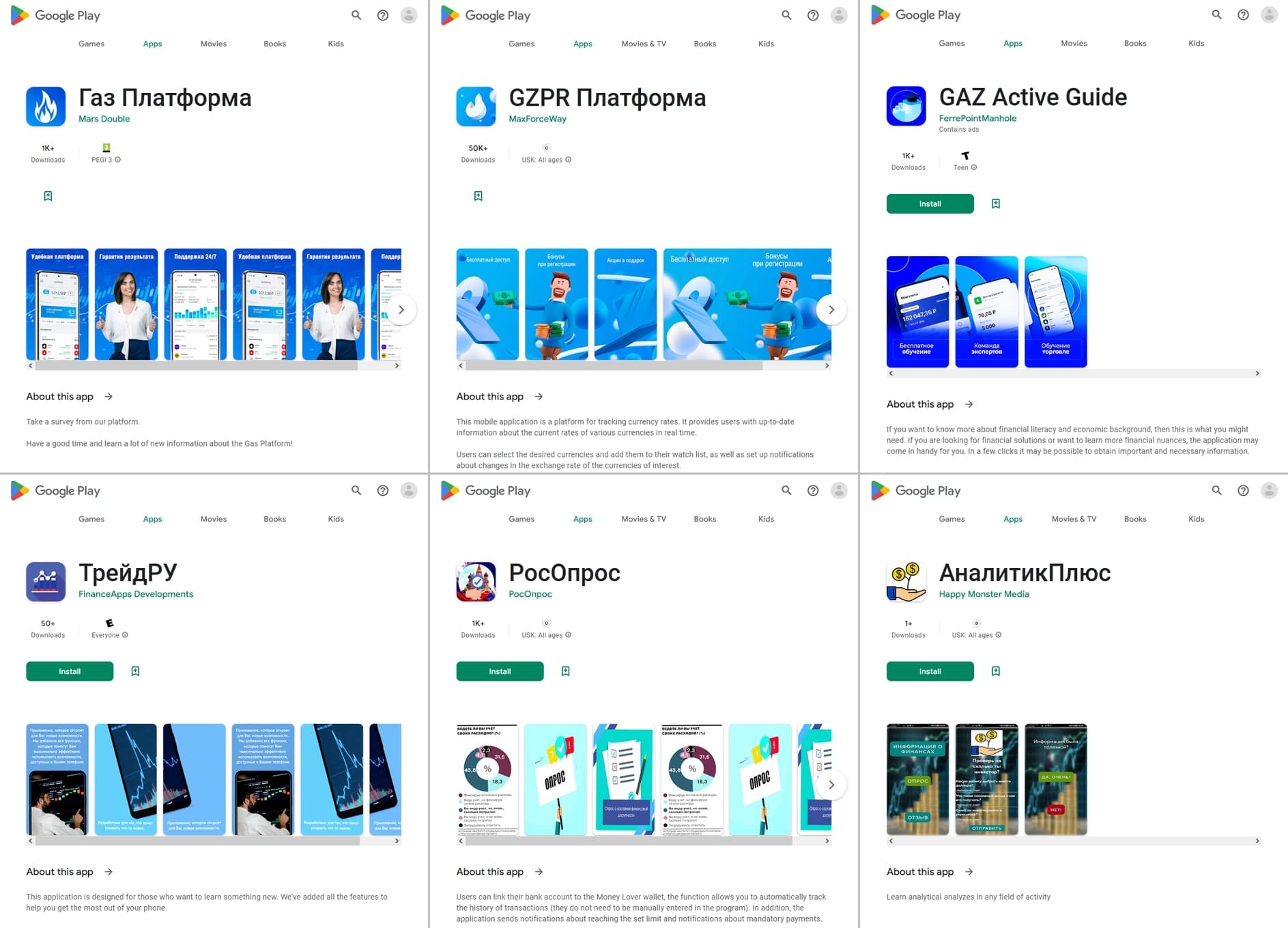
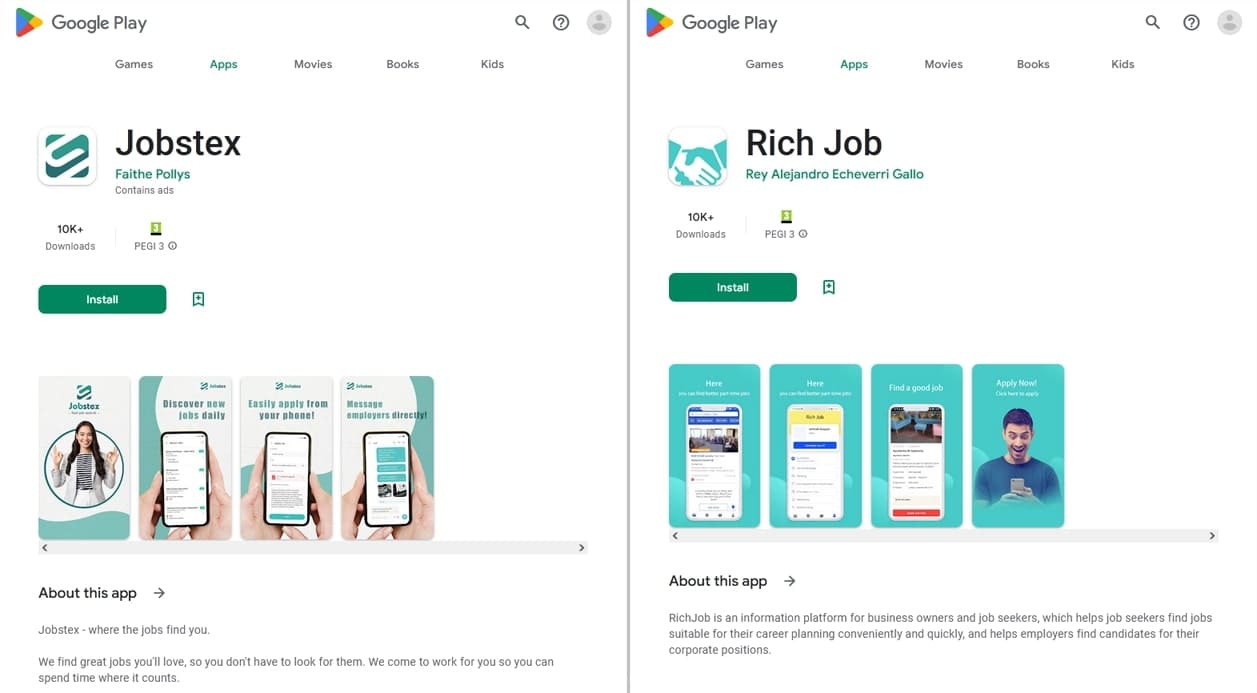
In April, Doctor Web’s malware analysts discovered over 30 malicious apps from the Android.FakeApp trojan family on Google Play. Some of them (like Android.FakeApp.1320, Android.FakeApp.1329, Android.FakeApp.1331, Android.FakeApp.1336, Android.FakeApp.1340, Android.FakeApp.1347, and others) were distributed under the guise of financial software. These included various reference books and investment teaching aids, trading instruments, apps for participating in polls and surveys, and so on. However, their real functionality was to load fraudulent websites, which malicious actors used in attempts to collect their victims’ personal data and steal their money.
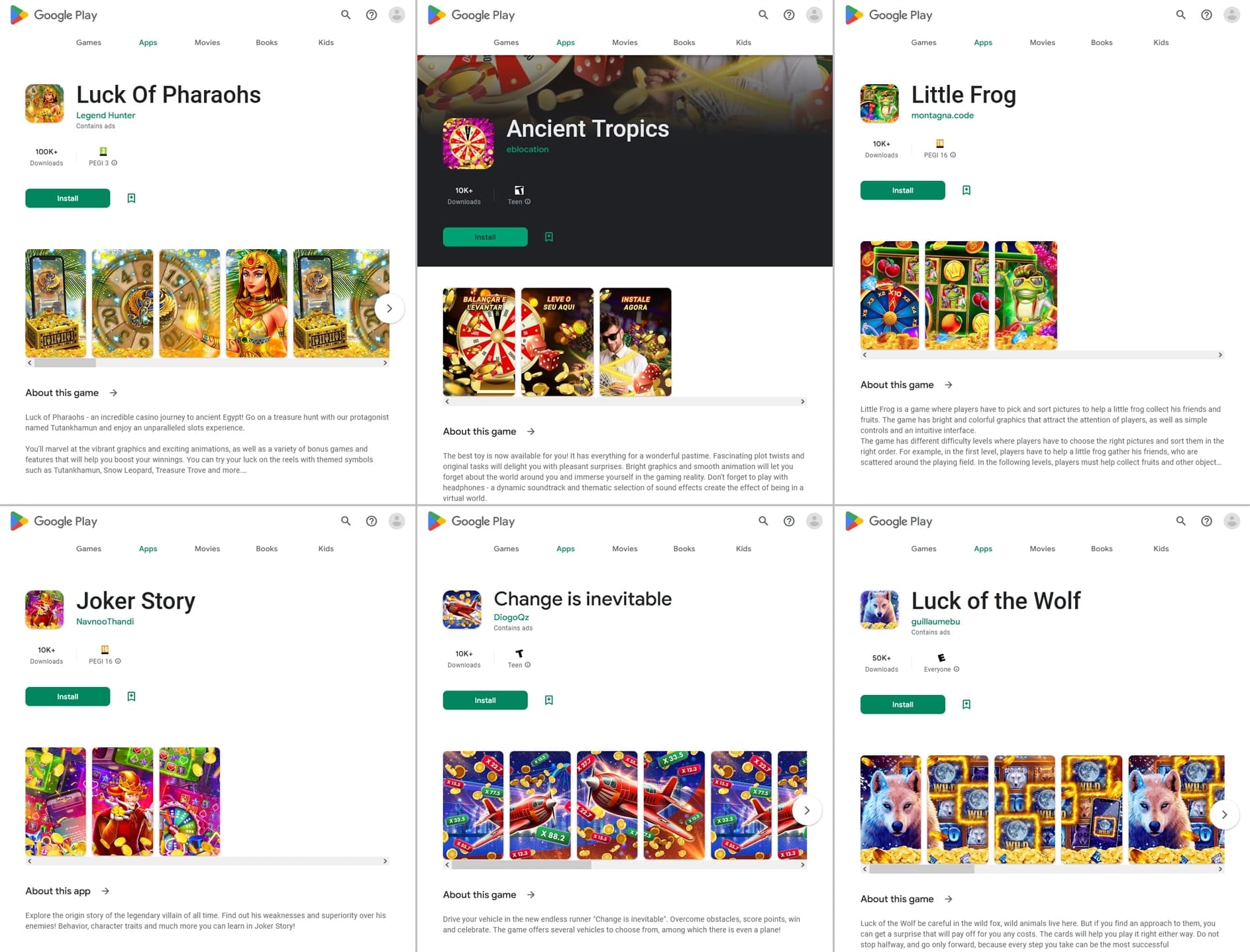
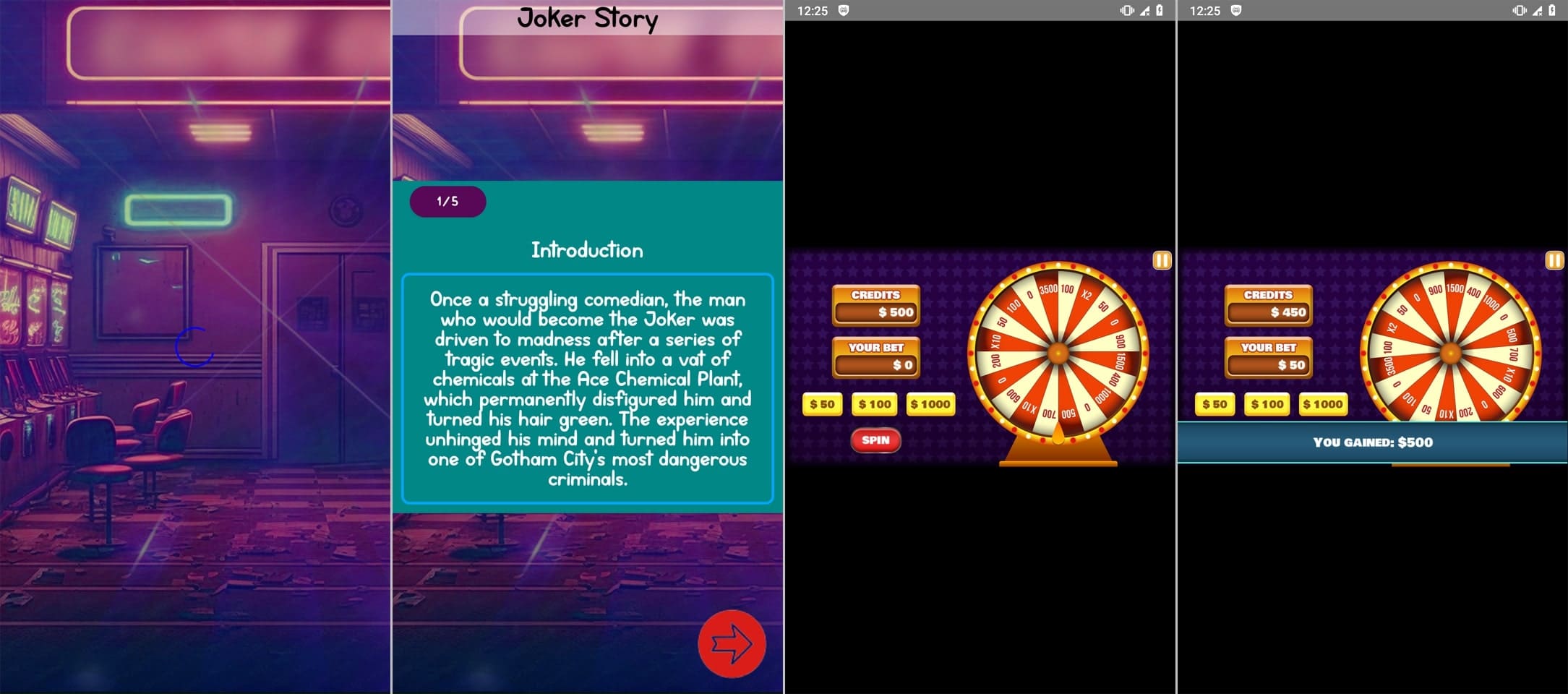
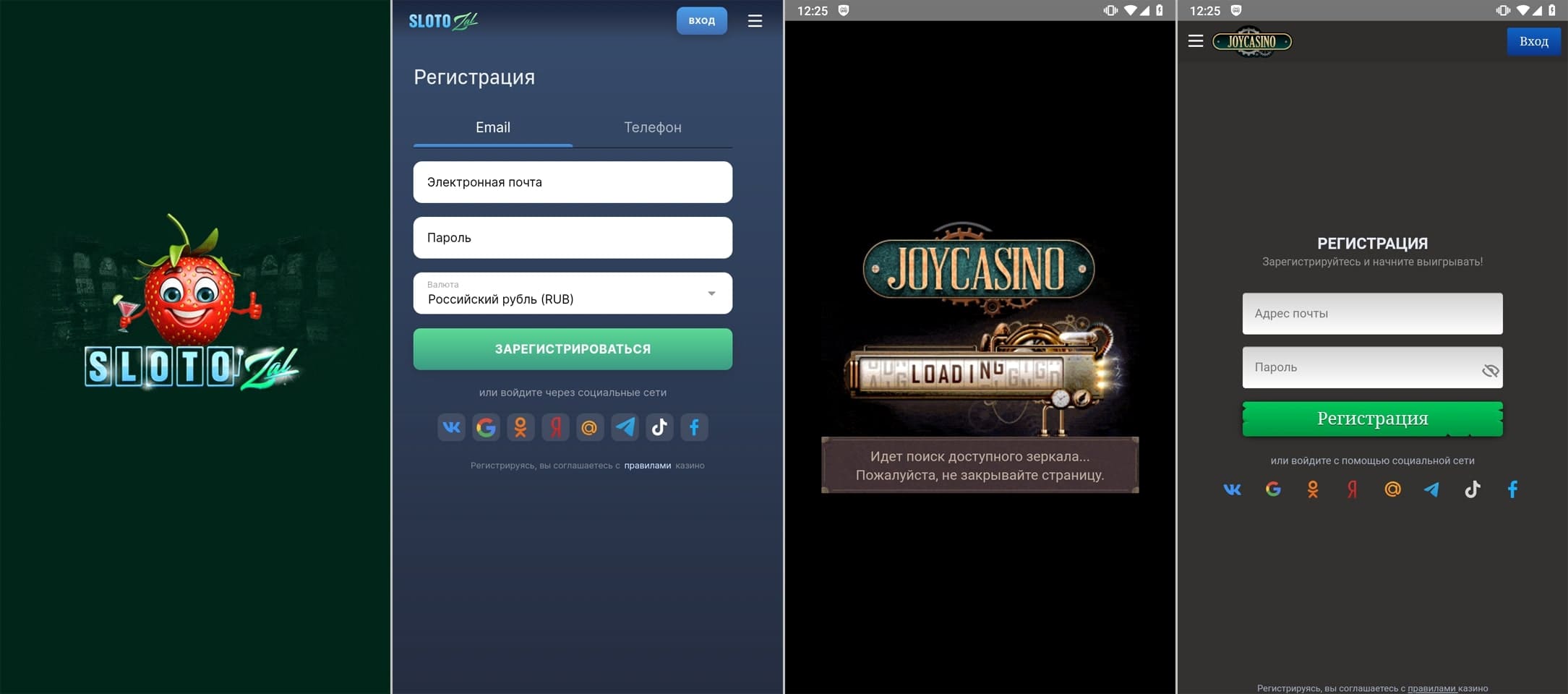
Fraudsters passed off other such programs, like Android.FakeApp.1322, Android.FakeApp.1326, Android.FakeApp.1330, Android.FakeApp.1334, Android.FakeApp.1337, and Android.FakeApp.26.origin, as games. But instead of the expected functionality, these programs could load online casino websites.
Examples of their two-sided nature are shown below. The first image depicts their ability to provide gaming functionality. The second one depicts how they load online casino websites.
In addition, our specialists discovered other fraudulent applications that malicious actors were distributing as job-search software. Dubbed Android.FakeApp.1307 and Android.FakeApp.1324, these members of the Android.FakeApp trojan family asked users to provide personal information by filling out a special form or to contact “employers” through messengers.
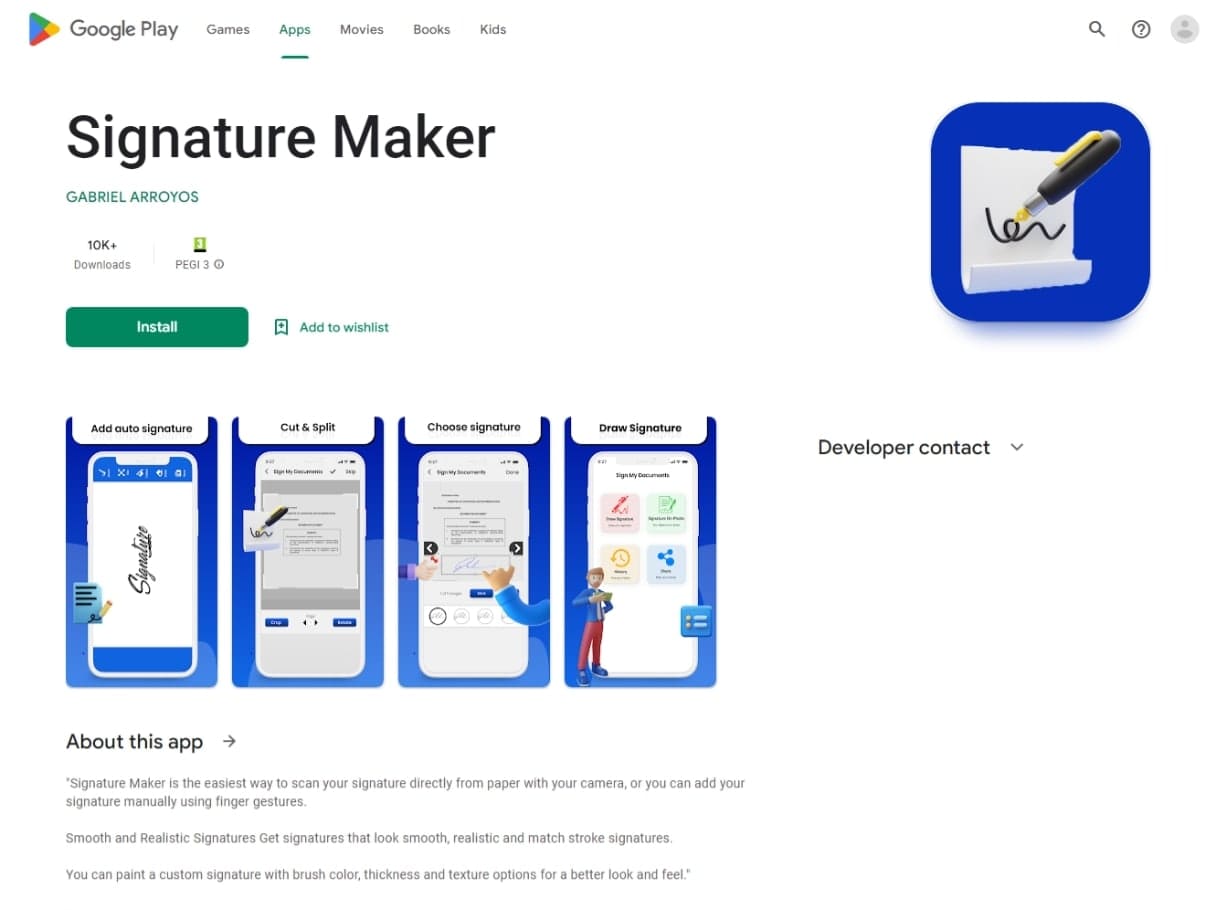
At the same time, attackers distributed the Android.Joker.2106 trojan app via Google Play. This piece of malware subscribed victims to paid services and was hidden in an app designed to create and work with signatures.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products