May 17, 2023
The number of banking trojan attacks increased by 78.47%. Users were most likely to deal with Android.BankBot trojan family members, which accounted for 73.06% of the detections of this type of threat. At the same time, the activity of ransomware malware from the Android.Locker family increased by 0.47%.
In addition, Doctor Web’s virus analysts discovered a large number of malicious apps from the Android.FakeApp family on Google Play. Threat actors used these in various fraudulent schemes. Moreover, our specialists identified cases where the system partition of an Android TV box model was infected with the dangerous Android.Pandora.2 backdoor. This piece of malware is capable of executing various malicious actions upon receiving commands from threat actors.
PRINCIPAL TRENDS IN MARCH
- An increase in adware trojan activity
- An increase in banking trojan and ransomware malware activity
- A decrease in spyware trojan activity
- An infected system partition for one of the Android TV box models
- The emergence of more threats on Google Play
Mobile threat of the month
In March, Doctor Web’s virus analysts identified cases where the system partition of a particular Android-based TV box model was infected with the Android.Pandora.2 backdoor. The Dr.Web anti-virus installed on the affected devices detected the new files in the protected file system area, and this trojan app was among those files. When commanded by malicious actors, Android.Pandora.2 can modify or completely replace the system hosts file (responsible for converting domain names into their corresponding IP addresses) to carry out DDoS attacks, download and install its own updates, and perform other malicious actions.
According to statistics collected by Dr.Web for Android
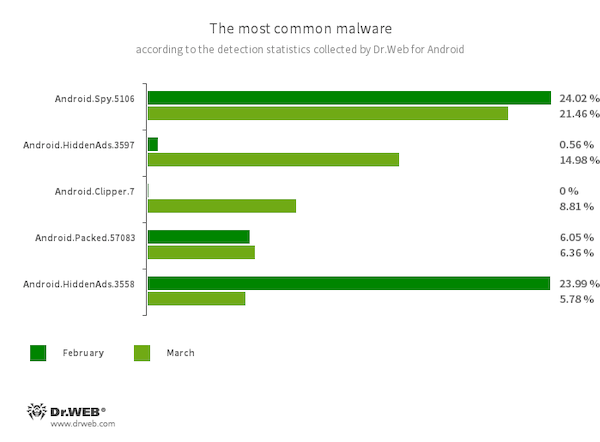
- Android.Spy.5106
- The detection name for a trojan that represents itself as modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes containing remotely configurable content.
- Android.HiddenAds.3597
- Android.HiddenAds.3558
- Trojan apps designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Clipper.7
- The detection name for some versions of the official applications from SHEIN and ROMWE - Ultimate Cyber Mall online stores. The affected variants of these apps contain a potentially dangerous functionality inherent to clippers, allowing them to copy information from the clipboard. They monitor the contents of the clipboard and, when a specific symbol sequence specific to URL addresses is detected, send the corresponding lines to a remote server.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
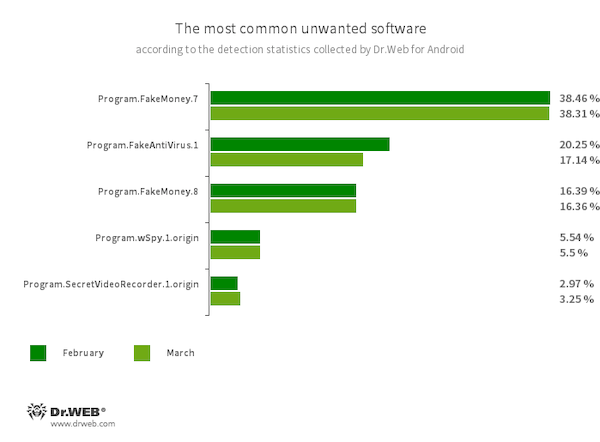
- Program.FakeMoney.7
- Program.FakeMoney.8
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to the phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
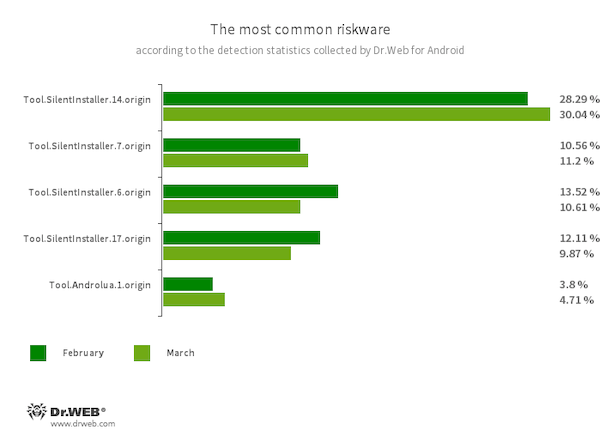
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.17.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Androlua.1.origin
- The detection name for some potentially dangerous versions of a specialized framework for developing Android software based on the Lua scripting language. The main logic of Lua-based apps resides in the corresponding scripts that are encrypted and decrypted by the interpreter upon execution. By default, this framework often requests access to a large number of system permissions in order to operate. As a result, the Lua scripts that it executes can potentially perform various malicious actions in accordance with the acquired permissions.
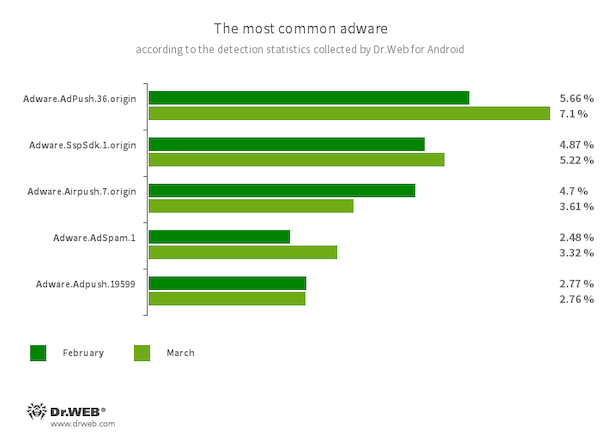
- Adware.AdPush.36.origin
- Adware.Adpush.19599
- Members of a family of adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, modules of this family collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.SspSdk.1.origin
- Adware.AdSpam.1
- These are specialized advertizing software modules that can be embedded into Android apps. They display ads when host applications are not being used and their windows are closed. As a result, users have a hard time identifying the source of such intrusive behavior on their devices.
- Adware.Airpush.7.origin
- A member of a family of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
Threats on Google Play
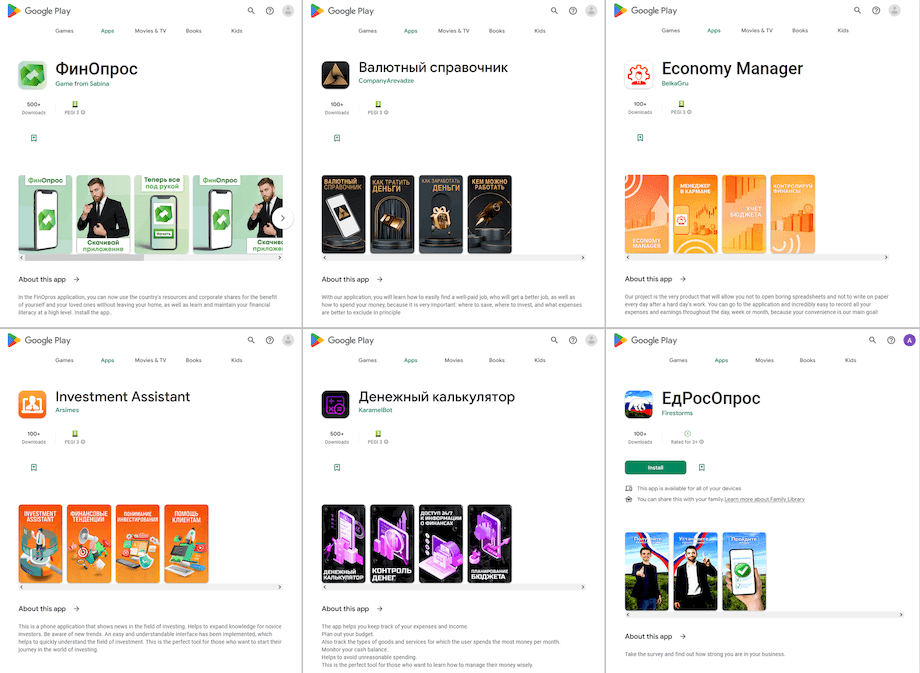
In March, Doctor Web’s specialists identified dozens of new trojan apps from the Android.FakeApp family on Google Play. They were distributed under the guise of different useful applications, but their real functionality was to load various websites. Many of these, like Android.FakeApp.1251, Android.FakeApp.1254, Android.FakeApp.1257, Android.FakeApp.1258, Android.FakeApp.1260, and Android.FakeApp.1294 cybercriminals passed off as financial software. For example, victims could download them as reference books and teaching aids, instruments for accessing investing platforms and trading different assets, programs for housekeeping, tools for taking polls and participating in surveys, and others. Such fake apps could load fraudulent sites where users were offered an alleged opportunity to access investing services by providing personal information and registering an account.
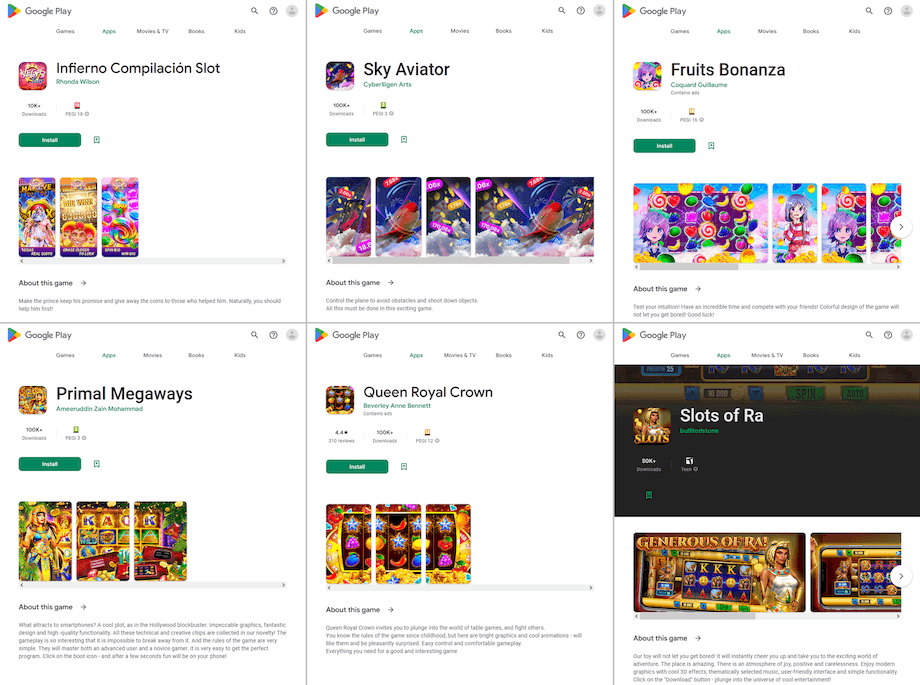
Other such programs, like Android.FakeApp.1252, Android.FakeApp.1255, Android.FakeApp.1268, Android.FakeApp.1272, Android.FakeApp.1278, Android.FakeApp.1280, Android.FakeApp.1297, and some others, were again distributed as different games. But instead of providing the expected functionality, they could load websites of online casinos.
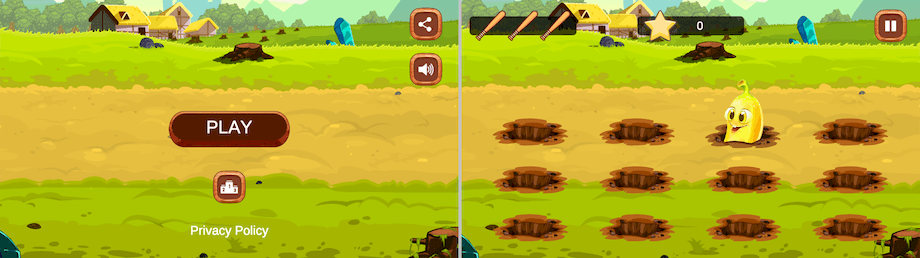
Below are examples of how such trojan apps would execute gaming functionality:
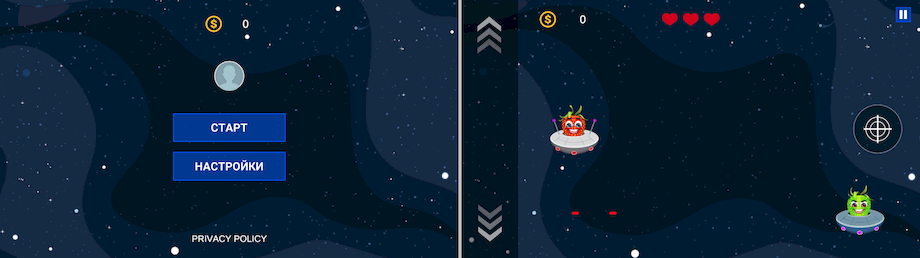
And examples of the casinos’ websites they could load:
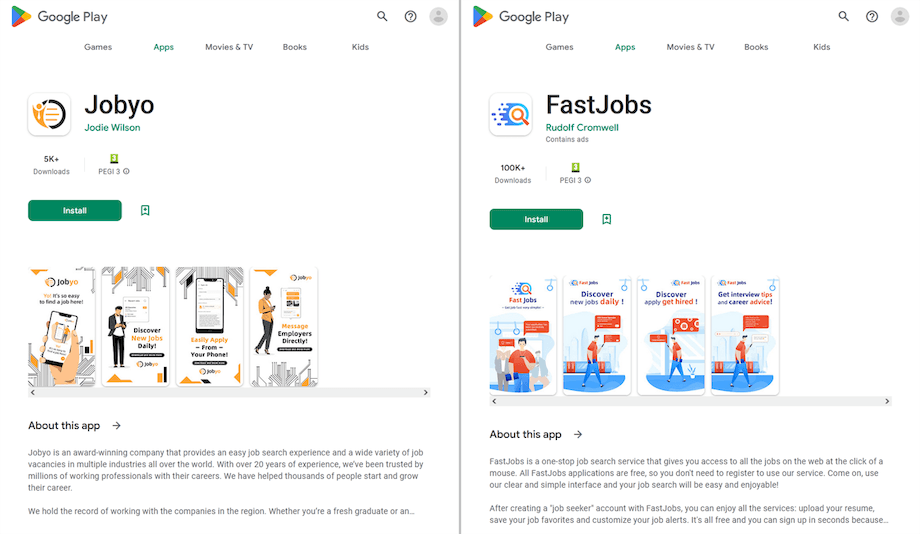
Our specialists also identified more fake programs disguised as job-search software. This malware loaded websites with a fake list of vacancies. Upon selecting the position they were interested in, potential victims were asked to fill out a special form by providing personal information or were offered to be put in touch with the “employer” via messengers like WhatsApp. Dr.Web detects these trojan apps as Android.FakeApp.1133 and Android.FakeApp.23.origin.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products